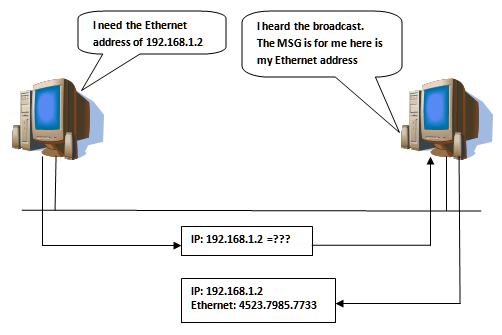
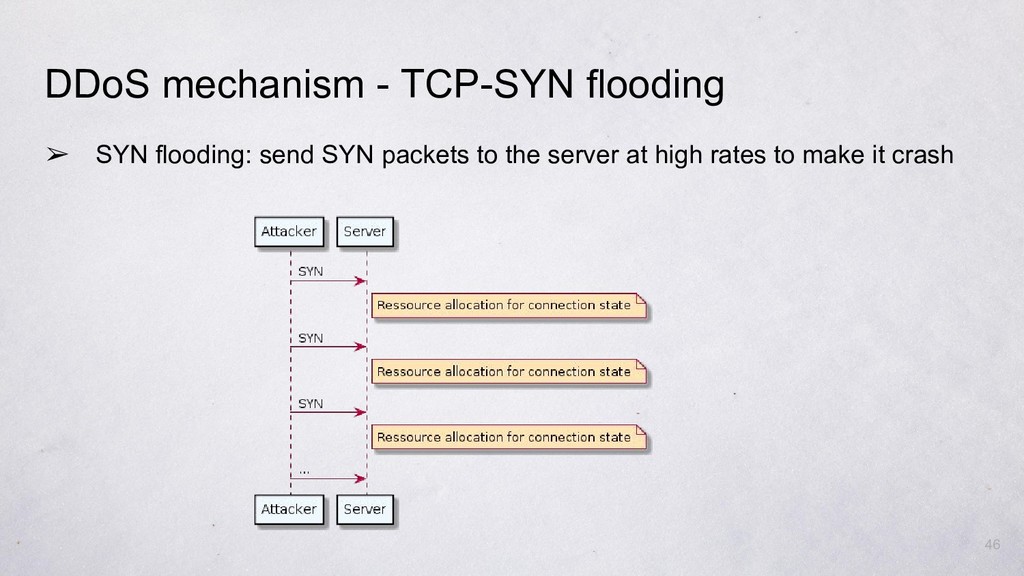
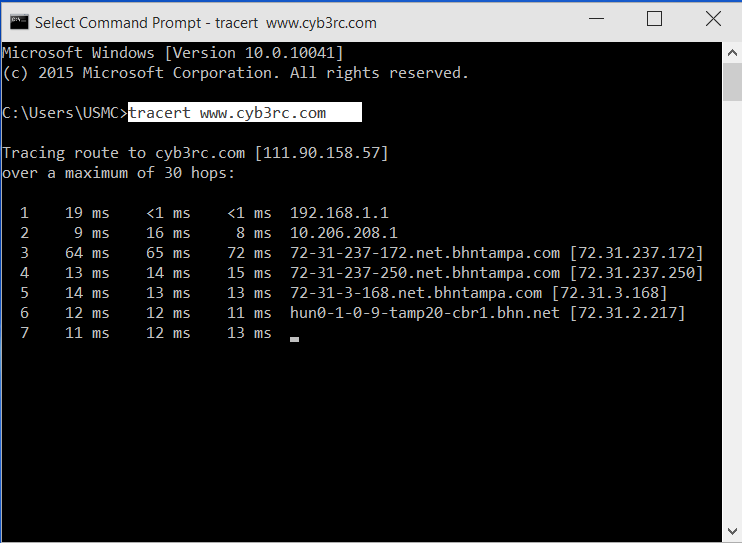
Hacker Fundamentals: The Everyman's Guide to How Network Packets Are Routed Across the Web « Null Byte :: WonderHowTo

How to hack a car — a quick crash-course | by Kenny Kuchera | We've moved to freeCodeCamp.org/news | Medium

How to hack a car — a quick crash-course | by Kenny Kuchera | We've moved to freeCodeCamp.org/news | Medium

Hackers can exploit USB to steal data | Science| In-depth reporting on science and technology | DW | 03.08.2014

Hacker Fundamentals: The Everyman's Guide to How Network Packets Are Routed Across the Web « Null Byte :: WonderHowTo