Cyber Security and Threats: Concepts, Methodologies, Tools, and Applications (3 Volumes): 9781522556343: Security & Forensics Books | IGI Global
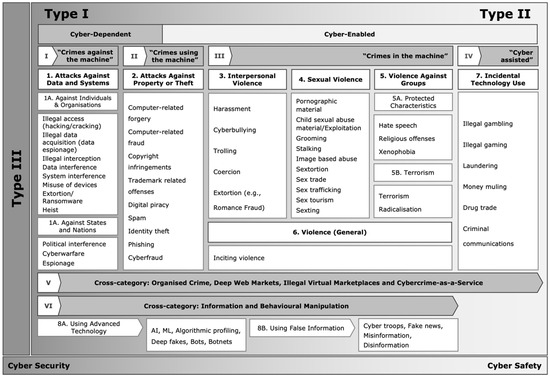
Forensic Sciences | Free Full-Text | Conceptualizing Cybercrime: Definitions, Typologies and Taxonomies
![PDF] Impact of ICT tools for Combating Cyber Crime in Nigeria Online Banking: A conceptual Review | Semantic Scholar PDF] Impact of ICT tools for Combating Cyber Crime in Nigeria Online Banking: A conceptual Review | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/ad464cedd5e6e03fcb6b65bc5968577589dda21c/5-Figure1-1.png)
PDF] Impact of ICT tools for Combating Cyber Crime in Nigeria Online Banking: A conceptual Review | Semantic Scholar

Cyber Security and Threats: Concepts, Methodologies, Tools, and Applications: Information Resources Management Association, Information Resources Management Association: 9781522556343: Amazon.com: Books