Export Checkpoint Firewall Policy to HTML/XML/Excel and Checkpoint Management Portal using cpdb2web tool - InfoSec Memo
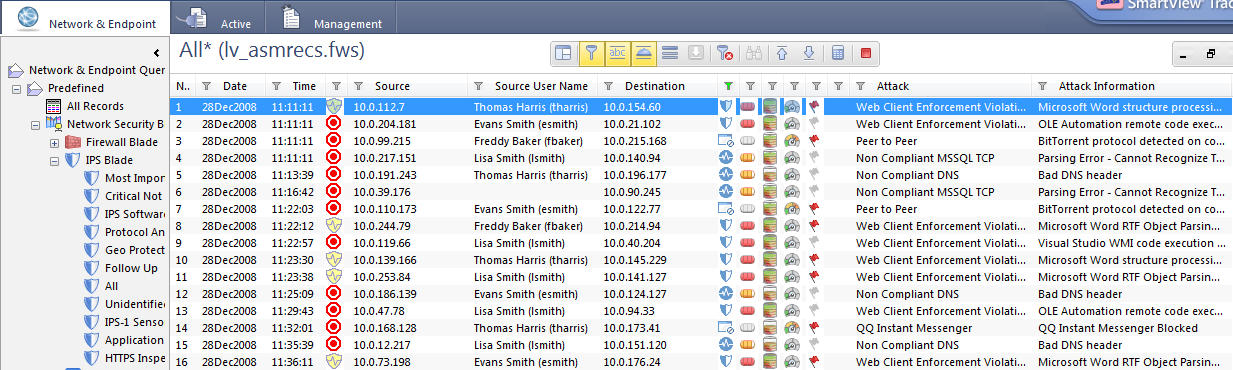
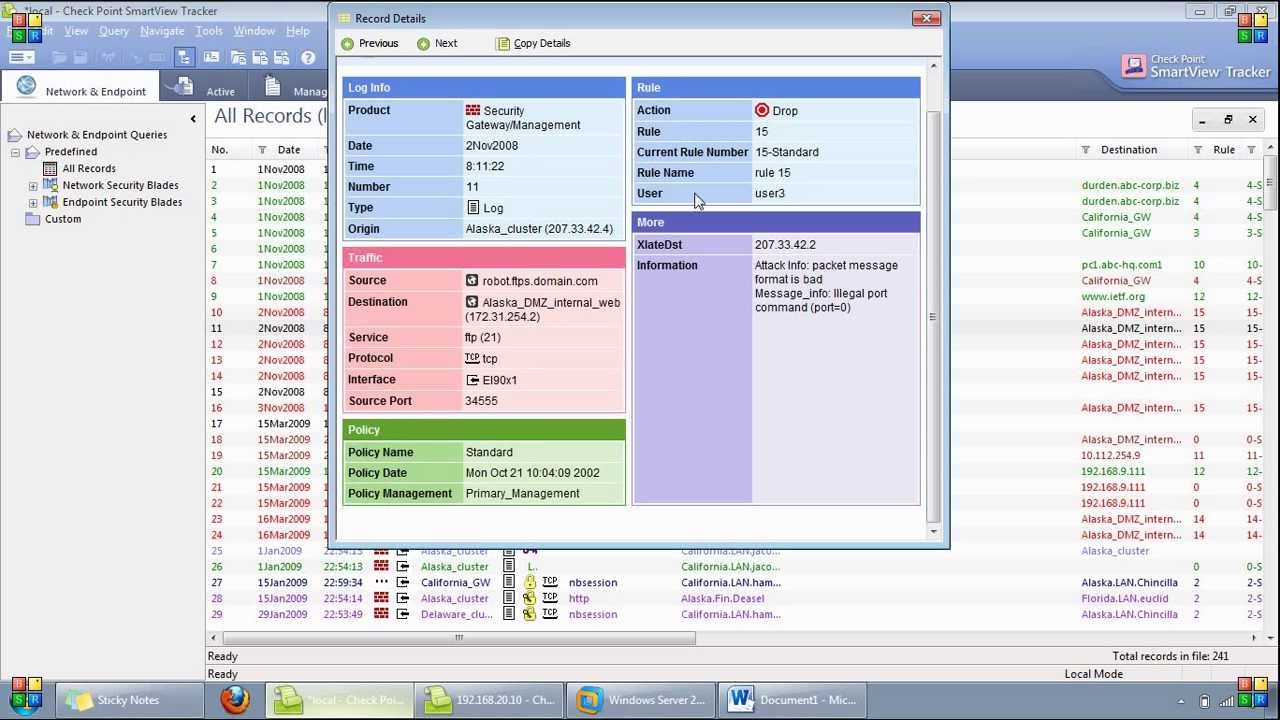
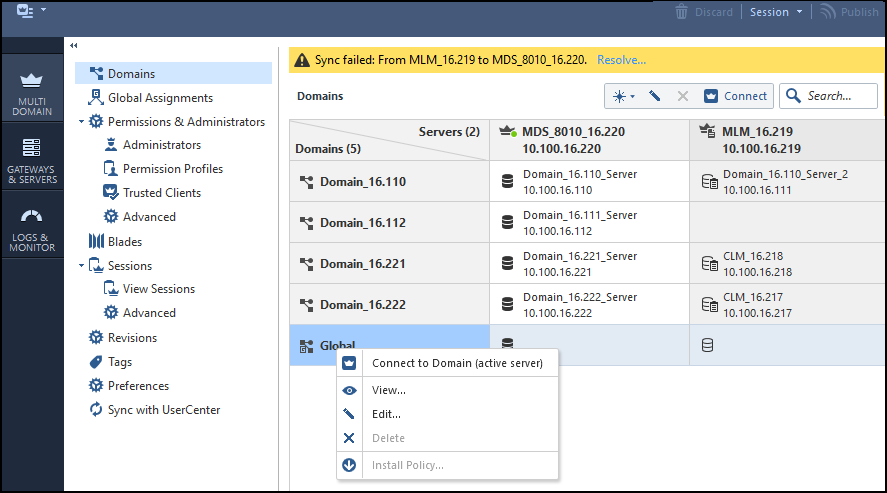
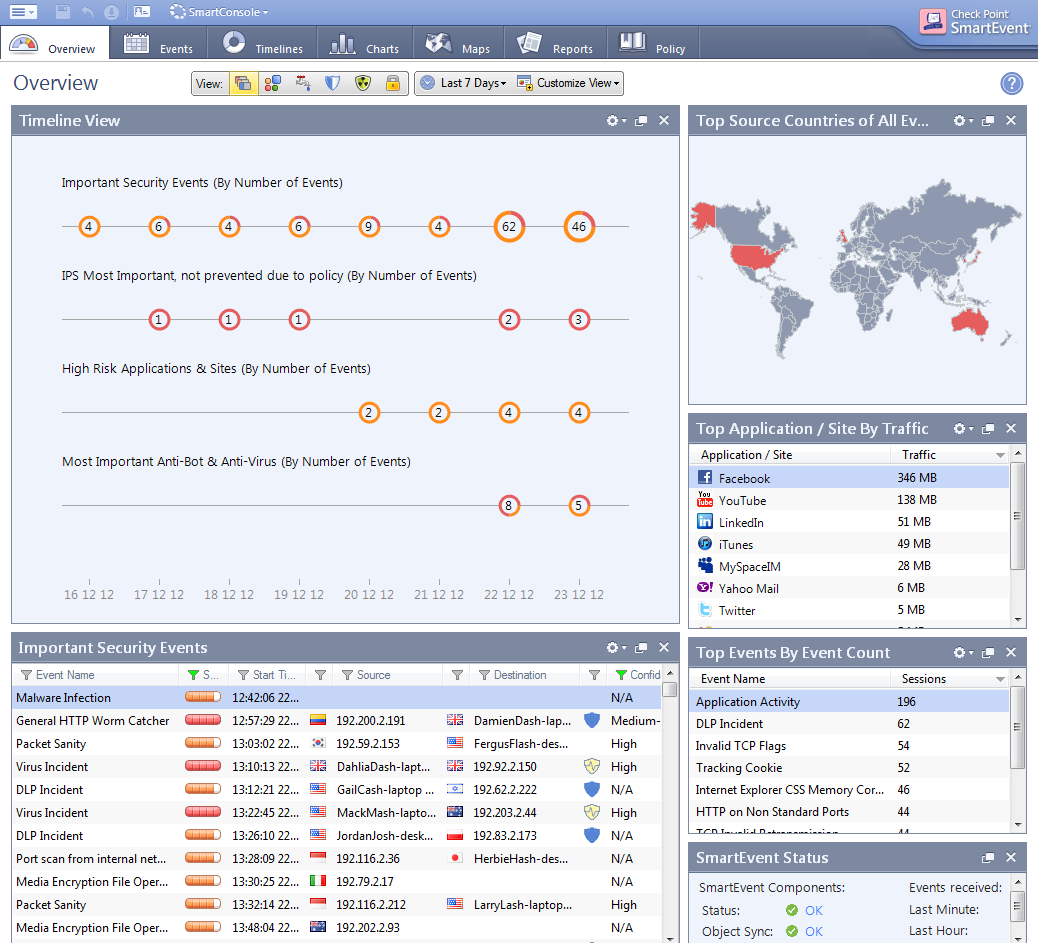
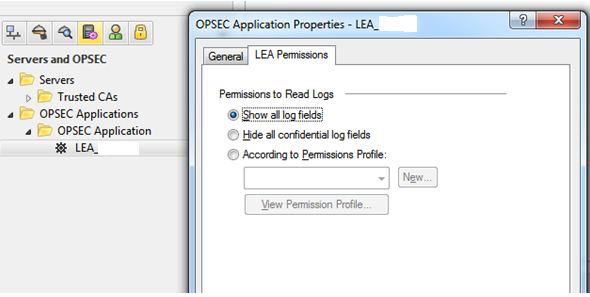
Troubleshooting Check Point logging issues when Security Management Server / Log Server is not receiving logs from Security Gateway