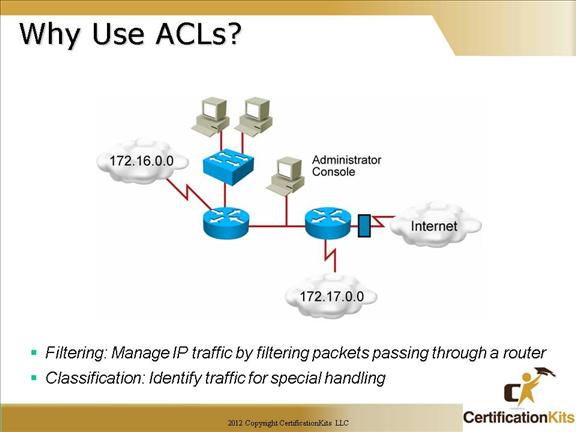
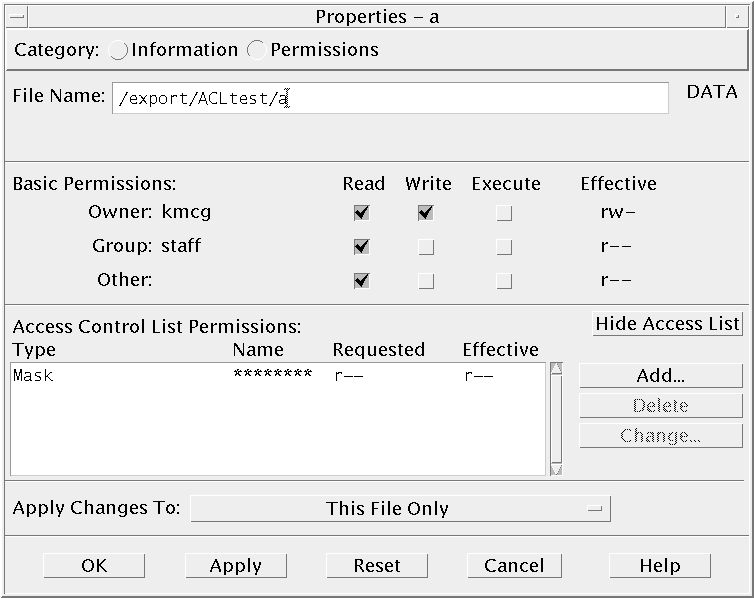
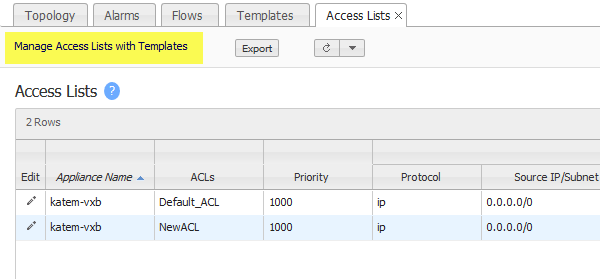
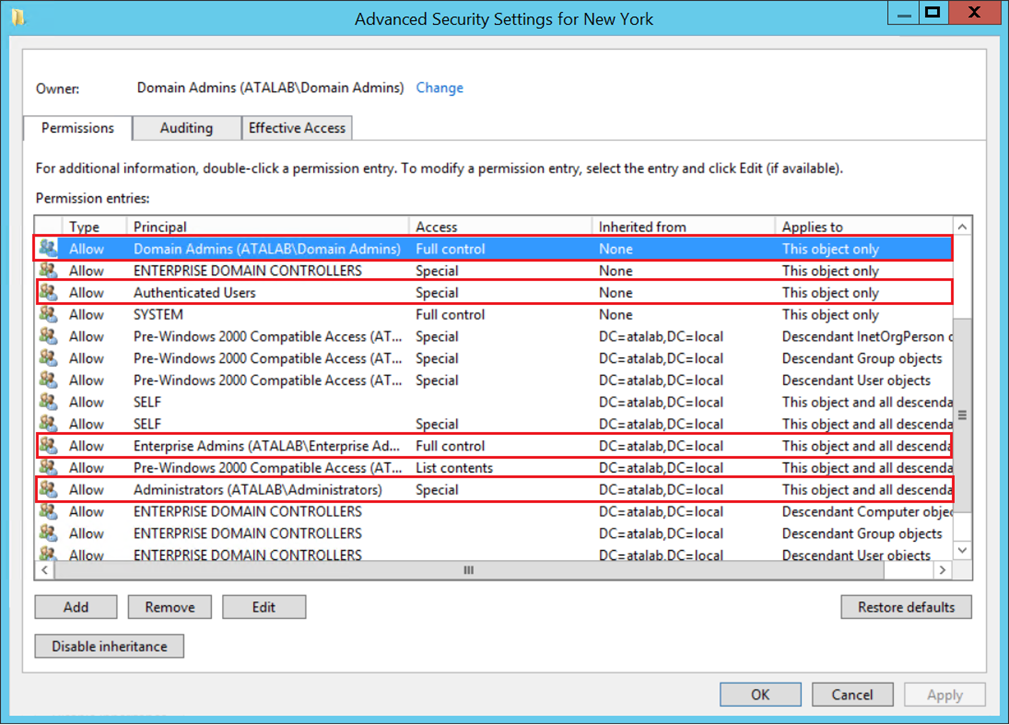
What is the Access Control List ( ACL ) and How to Create and Grant an ACL in Oracle Database Access Control List ( ACL ) | Create and Grant an ACL
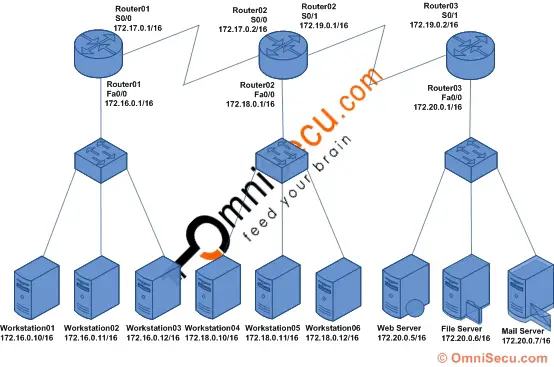
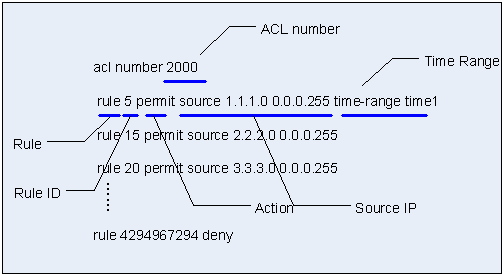
How to create and configure Extended Access Control Lists (ACL), access-list IOS command and access-group IOS command


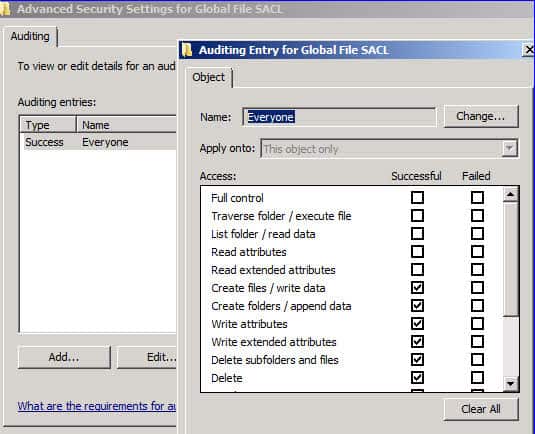


![acl [DokuWiki] acl [DokuWiki]](https://www.dokuwiki.org/_media/aclexample.png?w=400&tok=d65f7b)